So Your Username and Password Where in a Data Dump. Now What?
Whether it's Dropbox, LinkedIn, MySpace, PlayStation, or whatever the latest breach happens to be, it's almost inevitable that you will be caught up in one of these breaches and have your username, password and possibly other information exposed in a data dump. Here's how to respond when that happens.
How Does This Happen?⌗
A data dump is what often happens after a website has been breached and information about that site's users/customers is stolen. All that stolen data is often "dumped" on the Internet for all to see. Once the data is dumped, it's at that point that all this information becomes public and along with it, your information.
Sometimes, as in the case of the Ashely Madison dump, that information can be personally damaging. Other times the information is limited to usernames and passwords.
This article is going to focus on how to respond if your username and password are part of a data dump.
Step 1 - Reset Your Password⌗
This is obvious, but go and change your password. Do it right now, before something comes along and distracts you. Even if you're a security concious person and you're using Two-Factor Authentication (2FA), still go and change your password.
You're not done yet though! There is more you need to do to ensure there's no collateral damage.
Step 2 - Reset Shared Passwords⌗
Be honest now... did you reuse your original password on another site? Even just one?
One of the most common methods that someone can use to take over an account that you own is by using the password they found in a data dump. It works like this:
- A malicious person finds your username and password in a data dump. This person knows that password reuse is a very, very common habbit so they assume that they'll be able to get into other accounts you own using this password.
- They pick a target: maybe your email, maybe a social media account, or maybe your work.
- Through some ingenuity, research, or maybe via a weakness in the target, they're able to discover your username (or at least a list of probable usernames).
- They attempt to log into the target using the probable usernames and the password from the dump.
- If you've reused your password on the target, they are now in to your account.
This creates a very dangerous situation. Imagine that you've shared the same password with your online bank account and with the newest social media site you signed up to. Your bank (most likely... hopefully) has high security standards and is a very, very hard target for someone to breach. But what about the social media site? If a malicious person can breach the social media site, they could use that stolen information to attack a higher-value account such as your online bank. And unfortunately, this is not hypothetical. This is a real world strategy that attackers employ.
This is why Step 2 is so important: your exposure to the dump might be far greater than just the one site where the data was stolen from.
How do you find out which sites you've reused the password on? I can think of two options:
- You ask your password safe (aka, password manager) to give you a list of sites where you are using the same password.
- You guess.
If you use a password manager and can follow Option 1, then read on. If you find yourself having to follow Option 2, I suggest you skip to Step 3 to learn about password safes and then come back and read the rest of Step 2.
Your password safe should (I hope) have a way to tell you which accounts are using a password that's also used by other accounts.
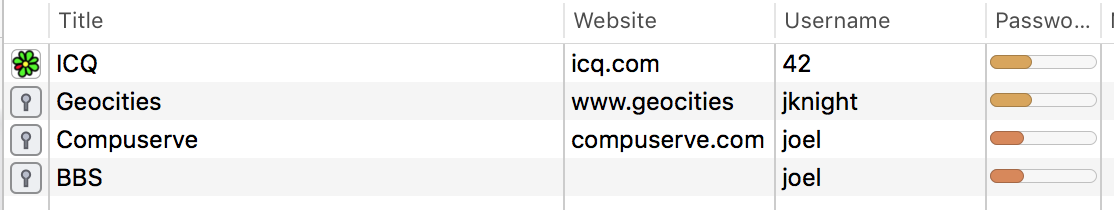
Now, my password safe doesn't tell me which account shares the specific password that was exposed in the data dump. It doesn't even tell me whether the passwords in the list all share the same password. It's just indicating that the listed accounts share a password with at least one other account in the list.
In order to fully protect against password reuse, the goal is to eliminate all of the accounts in this list by changing the password for each to something unique. When this is done, your exposure to a data dump is greatly reduced.
Step 3 - Forget Your Passwords⌗
The reason password reuse is so common is because our brains easily forget. We've got passwords for everything now and remembering a unique one for each account is nearly impossible.
The best way to handle passwords is to forget them. Don't try and store them in your brain. Instead, let your computer store them in a secure piece of software called a password safe (aka, password vault or password manager).
Just like a bank safe, your password safe is normally locked up in order to protect the contents inside. In order to use a password from within the vault, you unlock the vault by entering a vault password. This password becomes the one password you have to remember. It should be sufficiently long and unique since it's the key to the vault!
Besides storing all your passwords, your password safe software can do a couple other important things:
- Synchronize the safe across multiple devices. Your passwords can be with you on your computer, tablet and phone.
- Generate strong, unique passwords automatically.
Since the software can generate random passwords for you, there's no need to generate "unique" passwords on your own such as "Joel123", "Joel124", and so on. There's also no reason to pick a password that is probably already known to an attacker.
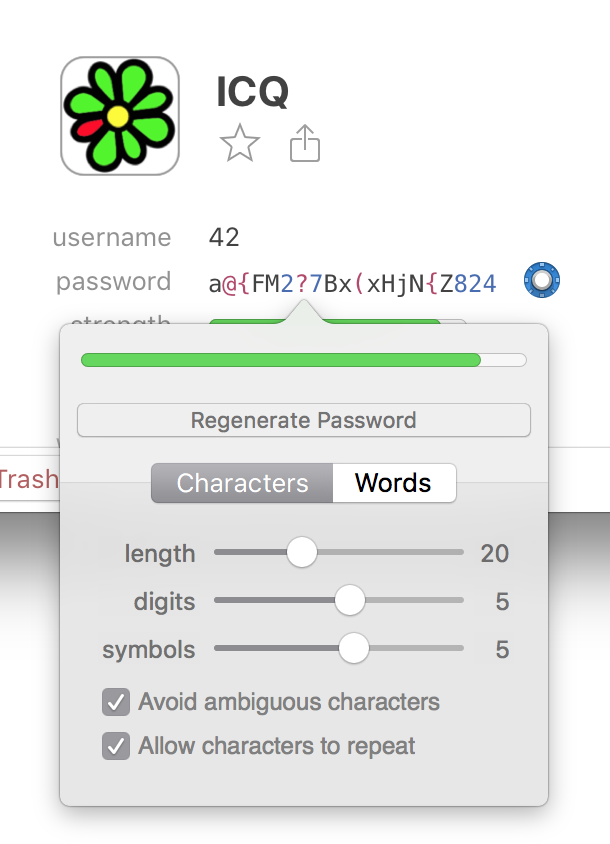
Also, since the safe will store this password and your brain doesn't have to, make it really long! And add digits and symbols to it. The more characters the generator has to choose from, the more random and unique the password can be. And the longer and more random the password, the greater the chances of being protected if this password shows up in a dump in the future.
Wrap Up⌗
This is the same advice I've verbally given to family and friends and so I thought I would write it down so I can share it with others as well. This advice isn't just for the ultra techie, this is for everyone. Password safes are easy to use and the higher end ones, especially if they offer a paid version, cater to the average, non-techie user.
We're all at risk of being caught up in a data dump so take some simple steps that can mitigate the impact and make yourself safer online.